1. Purpose
The purpose of a privacy policy is to articulate publicly that the agency will adhere to legal requirements and agency policy determinations that enable gathering and sharing of information to occur in a manner that protects personal privacy interests. This policy also covers the appropriate management of data and personal information as it relates to privacy. All Data Protection and Privacy related activities are performed and governed in accordance with Y&L’s Code of Business Conduct and any applicable policies.
2. Scope
This policy applies to all Y&L employees, contractors and partners doing business on behalf of Y&L, its divisions, businesses, functions, subsidiaries etc.
3. Policy
3.1 Handling Personal Information
The following principles apply to the collection, use, storage, disclosure of, and access to sensitive and/or personal information:
• Y&L will take all and use reasonable measures to store personal information securely.
• The collection of personal information must relate directly to the employment and compensation of employees and contractors or where required in the operation of the business.
• Sharing of personal information for tax, benefits, insurance, or other business-related activities, must only be done through Y&L secure file transfer methods
• Individuals must be informed of the purpose for which personal information is obtained, transmitted, or shared.
• Personal information will only be used for necessary business transactions and not for any other use.
• Personal information will not be released unless specifically requested through Human Resources or if required by law.
3.2 Handling Sensitive Business Information
• Sensitive information that if made public might have a considerable impact on Y&L Business, competitive advantage or public perception should be labeled as Confidential.
• All other information that is not publicly known should be labeled as For Internal Use Only.
• Sharing of files containing sensitive and/or business information with Y&L employees and business partners must only be done through secure email or file transfer methods.
• Internal work procedures, Development, Information Resources used for coding are Intellectual Property (IP) of Y&L Technologies and are critical elements to be protected from sharing, distributing or accidental exposure to un-authorized internal (Y&L) resources or Non-Y&L personnel.
3.3 Data Collection and Monitoring
Information is monitored at Y&L for the protection of our employees’ personal information. Systems used to monitor networks, systems and data are administered according to IT Security access policies and access is limited to those requiring access for their specific job related duties. Collection of personal information by, and their disclosure to, governmental agencies and authorities will be carried out only on the basis of specific business needs.
4. Data Privacy Procedures
4.1 Security procedure for Data Leakage Prevention
Y&L’s security practices are based on Information Security Management System (ISMS) standards. The principal objective of Information Security Management System (ISMS) is to protect the Intellectual Property Rights (IPR) of the customer and the organization. Information Security is characterized as the preservation of:
• Confidentiality: Ensuring that information is accessible only to those authorized to have access;
• Integrity: Safeguarding the accuracy and completeness of information and processing methods;
• Availability: Ensuring that authorized users have access to information when required;
• At Y&L, Data Leak Prevention (DLP) is designed to detect the potential data breach though implementation of monitoring data while in use in end user system through Web Sense which is implemented across the organization and the end user systems are not allowed the use of Instant messaging, web mail such as Yahoo, Gmail etc., in addition to laptops monitoring for any data leaving via removable devices, such as floppies, CDs, USB’s etc.
Additionally, DLP is designed to protect the data while in network though implementation for firewall, intrusion detection systems and data at storage through daily incremental and weekly full Backups using Symantec tools.
All employees have to mandatorily undergo training on ISMS every six months, while the Information Security team does the effective marketing of security to all managers and employees in distribution of guidance on information security policy, procedures, guidelines and standards to all employees and contractors. Not all Personal Identifiable Information (PII) is protected in the same way, but appropriate safeguards to protect the confidentiality of PII based on the PII confidentiality impact level. Some PII does not need to have its confidentiality protected, such as information that the organization has permission or authority to release publicly (e.g., an organization‘s public phone directory).
• Creating Policies and Procedures – comprehensive policies and procedures for protecting the confidentiality of PII.
• Conducting Training –The various functions within the company should reduce the possibility that PII will be accessed, used, or disclosed inappropriately by requiring that all individuals receive appropriate training before being granted access to systems containing PII.
• De-Identifying PII. Organizations can de-identify records by removing enough PII such that the remaining information does not identify an individual and there is no reasonable basis to believe that the information can be used to identify an individual. De-identified records can be used when full records are not necessary, such as for examinations of correlations and trends.
• Access Enforcement – Use of control access to PII through access control policies and access enforcement mechanisms (e.g., access control lists).
• Implementing Access Control for Mobile Devices – The company prohibits or strictly limit access to PII from portable and mobile devices, such as laptops, cell phones, and personal digital etc.,
• Providing Transmission/network Confidentiality – This is accomplished by encrypting the communications or by encrypting the information before it is transmitted and password protected as well.
• Auditing Events – Periodic audits, audit trails and monitor events that affect the confidentiality of PII, such as inappropriate access to PII.
4.2 Security breach notifications as required under various National/State laws
A data breach occurs when there is a loss or theft or unauthorized access to data that results in the potential compromise of the confidentiality or integrity of data. In the event that an IT staff member detects any kind of security breach, standard practice requires that the staff member contact the appropriate people listed on the company portal and report the incident.
Computer security incident response is an important component of information technology programs. Preventative activities based on the results of risk assessments will lower the number of incidents, but not all incidents can be prevented. An incident response capability is therefore necessary for rapidly detecting incidents, minimizing loss and destruction, mitigating the weaknesses that were exploited, and restoring computing services.
Breaches involving PII are harmful to both individuals and organizations. Harm to individuals and organizations is contained and minimized through the development of effective incident response plans for breaches involving both regular Incidents and PII as well. The Plan include elements such as determining when and how individuals should be notified, how a breach should be reported, and whether to provide remedial services to affected individuals.
An incident response capability at Y&L includes the following actions:
• An incident response policy and plan
• Procedures for performing incident handling and reporting
• Setting guidelines for communicating with outside business partners regarding incidents
• A well-defined team structure and staffing model
• Relationships between the incident response team and other groups, both internal and external.
• What services the incident response team should provide
• Staffing and training the incident response team.
Incident response to Data breach involves four phases –Preparation, detection and analysis; Containment, eradication, and recovery; and post-incident activity.
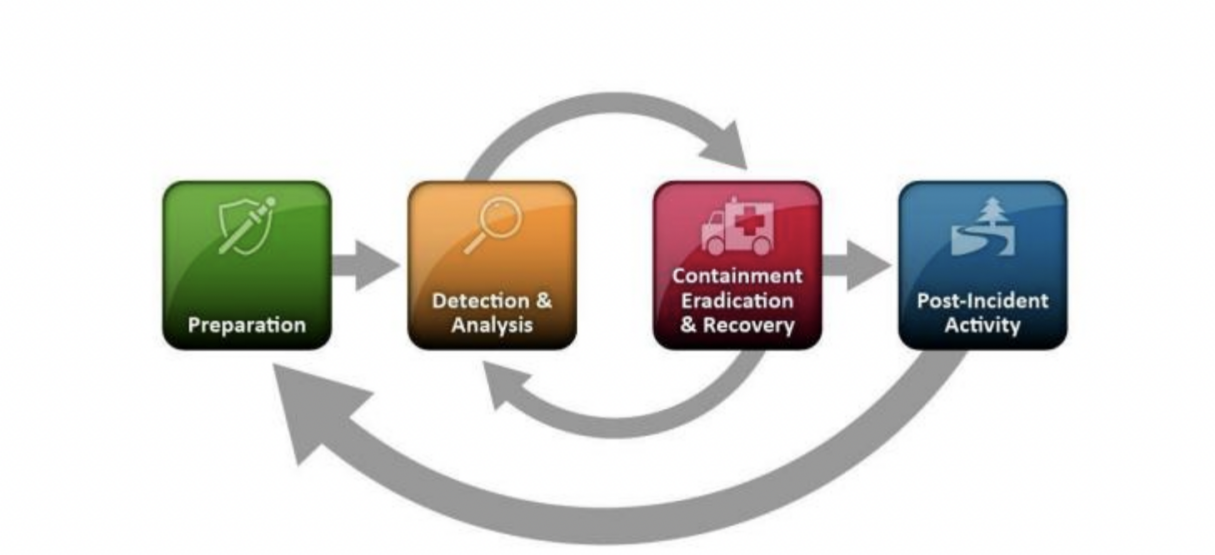
INCIDENT RESPONSE LIFE-CYCLE
• Preparation – Preparing to handle Incidents. Incident response methodologies typically emphasize preparation—not only establishing an incident response capability so that the organization is ready to respond to incidents, but also preventing incidents by ensuring that systems, networks, and applications are sufficiently secure.
• Detection and Analysis: ISMS defines the detection and analysis technologies and techniques for handling incidents. Incidents categories includes such as:
o External/Removable Media: An attack executed from removable media or a peripheral device.
o An attack that employs brute force methods to compromise, degrades or destroys systems, networks, or services.
o Web: An attack executed from a website or web-based application.
o Email: An attack executed via an email message or attachment.
o Improper Usage: Any incident resulting from violation of an organization’s acceptable usage policies by an authorized uses.
o Loss or Theft of Equipment: The loss or theft of a computing device or media used by the organization, such as a laptop etc.
• Containment, Eradication and Recovery: The first priority after any type of breach is discovered / analyzed and contains the breach, the data must be secured, and the integrity, security, and confidentiality of the data or data system must be restored. An essential part of containment is decision making (e.g., shut down a system, disconnect it from a network, and disable certain functions).
o Potential damage to and theft of resources o Need for evidence preservation
o Service availability (e.g., network connectivity, services provided to external parties) o Time and resources needed to implement the strategy
o Effectiveness of the strategy (e.g., partial containment, full containment)
o Duration of the solution (e.g., emergency workaround to be removed in four hours, temporary workaround to be removed in two weeks, permanent solution).
After an incident has been contained, eradication may be necessary to eliminate components of the incident, such as deleting malware and disabling breached user accounts. In recovery, system administrators restore systems to normal operation and remediate vulnerabilities to prevent similar incidents.
Recovery involves such actions as restoring systems from clean backups, rebuilding systems from scratch, replacing compromised files with clean versions, installing patches, changing passwords, and tightening network perimeter security (e.g., firewall rule sets, boundary router access control lists)
• Post Incident Activity: Lessons Learned, Using Incident Data
o Lessons learned activities will produce a set of objective and subjective data regarding each incident. Over time, the collected incident data will be useful in several capacities.
4.3 Disposal of Personally Identifiable Information (PII) when the data is no longer relevant.
ISMS at Y&L defines personally identifiable information (PII), which if lost, compromised, or disclosed without authorization, could result in substantial harm, embarrassment, inconvenience to an individual. PII is any information about an individual maintained by an company including (a) any information that can be used to distinguish or trace anindividual‘s identity, such as Permanent Account Number (PAN), Social security number, date and place of birth, or personnel records; and (b) any other information that is linked or linkable to an individual, such as medical, educational, salary, financial, and employment information.
Examples of PII include:
• Name, such as full name, maiden name, maiden name, or alias
• Personal identification number, such as Permanent Account Number, Social security number (SSN), passport number, driver‘s license number, taxpayer identification number, or salary/financial account or credit card number
• Address information, such as street address or email address
• Personal characteristics, including photographic image, fingerprints, or other biometric data (e.g., retina scan, voice signature, facial geometry)
• Information about an individual that is linked or linkable to one of the above (e.g., date of birth, place of birth, race, religion, activities, geographical indicators, employment information, medical information, education information, financial information)
It is the responsibility of Human Resources, Project development team and Information Security departments to protect information that has been entrusted to Individuals and business and an important part of their duty is to ensure that all sensitive date is properly used, protected from unauthorized use, and securely dispose the personally identifiable information (PII) when data is no longer relevant.
Data protection involves three stages – Encrypting Sensitive data, Securing Sensitive personal information when it is not in use and Disposing of Sensitive information.
All sensitive data is encrypted using WinZip and stored in a centralized location which is accessible only to authorized users. Sensitive PII, including archived emails, will be destroyed or erased permanently when retention of the data is no longer required, consistent with organization data retention policy. Printed materials are shredded and laptops are sanitized before re-use.
Y&L’s minimize the use, collection, and retention of PII to what is strictly necessary to accomplish the business purpose and objective. The likelihood of harm caused by a breach involving PII is greatly reduced if an organization minimizes the amount of PII it uses, collects, and stores. Also, we regularly review the holdings of previously collected PII to determine whether the PII is still relevant and necessary for meeting the organization‘s business purpose and objectives. Such as:
• Review current holdings of PII and ensure they are accurate, relevant, timely, and complete
• Reduce PII holdings to the minimum necessary for proper performance of company functions
• Develop a schedule for periodic review of PII holdings once every six months. • Establish a plan to eliminate the unnecessary collection and use of SSNs.
4.4 Privacy Impact Assessments (PIAs)?
PIA’s are undertaken based on whenever business needs and the main purpose of conducting a Privacy Impact Assessment is to protect the personally identifiable information from losses of confidentiality and Integrity. The processes of identifying PII are comprised of questionnaires that are completed by the business owners in collaboration with the system or data owner. And this is initiated by the information security officer when a new engagement or a project kicks off.
PII is evaluated to determine its PII confidentiality impact level, so that appropriate safeguards can be applied to the PII. The procedure laid out describes the process that Y&L follows or in other words considers when determining the PII confidentiality impact level. The following are examples of factors:
o Identification -Evaluate how easily PII can be used to identify specific individuals. For example, a SSN uniquely and directly identifies an individual, whereas a telephone area code identifies a set of people.
o Quantity of PII – How many individuals can be identified from the PII. The PII confidentiality impact level will be raised and not lowered based on this factor.
o Data Field Sensitivity – Evaluate the sensitivity of each individual PII data field. For example, an individual‘s SSN or Salary/Financial account number is generally more sensitive.
o Evaluate the context of use—the purpose for which the PII is collected, stored, used, processed, disclosed, or disseminated. The context of use may cause the same PII data elements to be assigned different PII confidentiality impact levels based on their use. If the confidentiality of the lists is breached, the potential impacts to the affected individuals and to the organization are significantly different for each list.
o Obligations to Protect Confidentiality. The Company that is subjected to any obligations to protect PII should consider such obligations when determining the PII confidentiality impact level. Obligations to protect generally include laws, regulations, or other mandates (e.g., Privacy Act). For example, some Federal agencies, such as the Census Bureau and the Internal Revenue Service (IRS), are subject to specific legal obligations to protect certain types of PII.
o Access to and Location of PII. Organizations may choose to take into consideration the nature of authorized access to and the location of PII. When PII is accessed more often or by more people and systems, or the PII is regularly transmitted offsite, then there are more opportunities to compromise the confidentiality of the PII.
That being said, The PII confidentiality impact level is derived from the data obtained and classified as—low, moderate, and high which indicates the potential harm that could result to an individuals and the organization if sensitive Personal information are accessed, used, or disclosed. Privacy Impact analysis are submitted to an organization‘s Information security office for review and approval.
4.5 Process for identifying Data Privacy issues or privacy related content from Customers.
Any sensitive information about an individual maintained by the company (e.g., date of birth, place of birth, caste, geographical locations, employment information, medical or health information, background checks, Salary information, PAN or Social Security Number) is termed as Personally Identifiable Information (PII).
Y&L can provide to customer a leveraged security team including a Lead Information Risk Manager and Compliance Assurance Manager, who will interact with all relevant customer security and compliance functions. The Security Governance Framework in conjunction with the additional security service will allow for all aspects of security in relation to SAP, to be managed and developed.
The Security Risk Manager has the following responsibilities:
o Coordinate the investigation and management of, as well as the response to, all security matters that occur.
o Coordinate vulnerability assessments and scanning, and oversee intrusion detection and monitoring activities, in coordination with Customer security IT staff.
o Support the Account Executive (AE) for security and compliance requirements that are external to service delivery, such as human resource (HR) issues affected by security incidents or PII.
o Exercise governance and management oversight of all Y&L operated security and compliance services.
o Maintain the overall Security Management Plan (SMP) via the Incident Management Plan, tailored for the in-scope services and security incident escalation processes on the account.
o Review Customer security and compliance policies and procedures against the management of the SAP Application
o Develop, in conjunction with Customer, security and compliance strategies to anticipate future threats and requirements and define the strategic roadmap for any future services and technology.
The processes of identifying PII are comprised of comprehensive questionnaires that are completed by the business owners in collaboration with the system or data owner. Once data is obtained, a privacy Impact analysis is completed before the development/project related work begins. Privacy Impact analysis is submitted to an organization‘s Information security office for review and approval.
The following are some topics that are commonly gathered information through the use of PIA:
• What information is to be collected
• Why the information is being collected
• The intended use of the information
• With whom the information will be shared
• How the information can be secured
• What choices the company has to make regarding an IT system or collection of information as a result of performing the PIA.
• Whether breach notification to affected individuals is required • Timeliness of the notification
• Source of the notification
• Contents of the notification
4.6 Procedures to communicate to the customers when there is an unauthorized access to a customer’s Personally Identifiable Information (PII)
Incident response is needed because attacks frequently compromise personal and business data. It is critically important to respond quickly and efficiently when security breaches occur. Incident response helps personnel and organization to minimize loss or theft of information and disruption of services caused by incidents. Another benefit of incident response is the ability to use information gained during incident handling to better prepare for handling future incidents and to provide stronger protection for systems. Besides the business reasons to establish an incident response capability, Organizations must comply with law, regulations, and effective defense against information security threats.
In the event of an unauthorized access to confidential or sensitive personal information, the information security office is notified, where-in ISO evaluates the nature of breach, level of impact and the potential harm that could result to an individual or a business.
Once the impact is analyzed, the information security officer establishes close coordination among personnel from across the organization – project/program management, system owner, data owner etc., and communicates to the customer within 4 business hours through Incident reporting method- Phone hotline, Conference Bridge or Management reporting structure.
The following are some topics that are reported through the use of standard Incident reporting method.
• To who (Person) should we report the incident, Date and time the incident covered
• Nature of the incident or Breach
• Level of Impact
• Name of system and possible inter-connectivity with other systems • Description of the information lost or compromised
• What type of information was lost or compromised
• Unauthorized use of the lost or compromised information
• Whether law enforcement to be contacted.
• Means of providing the notification
• Who receives the notification
• What actions were taken and by whom
5. Policy Enforcement
It is the responsibility of each employee to adhere to this Information Security Policy. Any Violation of this policy may result in revocation of access privileges to Y&L’s technology resources and appropriate disciplinary action by Y&L, up to and including termination of employment, contract, or engagement.
